Network Integrity: The Key to NFV
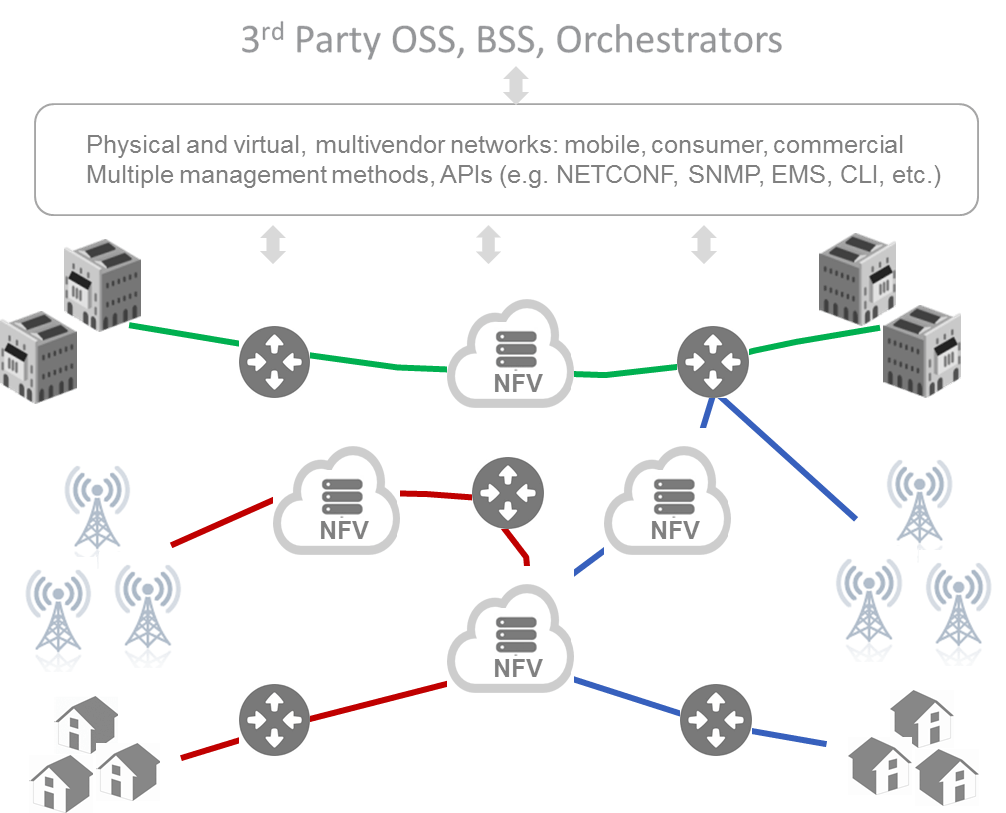
Assuring network data integrity in orchestrated networks is necessary for automation and end-to-end orchestration. The parameters, settings, and configurations of physical network functions (PNFs), virtual network functions (VNFs), and underlying network function virtualization infrastructure (NFVI) need to be matched with centralized OSS and orchestration systems. If data integrity is not synchronized, automated end-to-end service orchestration will fail. Because there will be more automated systems, orchestrators and humans programming the network, adjusting parameters, and configurations, the likelihood for poor network data integrity is increased. Given the heightened performance inter-dependencies between VNF and NFVI configurations to service quality and performance, there is an important need to continuously collect, audit, and compare data to “gold-standard” configuration templates.
Complementing real-time performance analytics, data network integrity analytics will help ensure orchestrators can make the correct, informed, and timely decisions. A scalable and automated auditing of data quality allow discrepancies to be easily identified and corrected. Data network integrity analytics can also be used as part of network planning an optimization processes when correlated with real-time performance analytics. Trends can be studied and new configurations, service parameters, and settings can be recommended based on predicted future demands or needs.
Because of the shared, multi-tenant nature of virtualized networks, maintaining security integrity is even more challenging. Multi-tenancy environments pose significant challenges when trying to maintain configuration integrity, and common cloud infrastructure could easily have hypervisor vulnerabilities introduced as a result of integrity failures. Virtual Machine, guest OS, or VNF manipulation could also compromise the integrity of the hypervisor. It will be important that logging and monitoring of hypervisor activities be performed. Similarly, it will be important that VNF configurations themselves are audited to understand whether configuration or operating system changes may have an impact to security integrity.
An important driver for NFV is to create a more flexible and elastic network to enable new service provider business models and revenue opportunities. VNFs will be instantiated, retired, or moved in a more dynamic fashion in order to meet the service delivery requirements. New business models could include VNF or VNF-as-a-Service whereby service providers could host different 3rd party VNFs within their own distributed, virtualized infrastructure. Some NFV implementations may involve hosting VNFs from different 3rd parties within a common service provider virtualized infrastructure. Without periodic integrity auditing, VNFs could be arbitrarily instantiated by Virtual Infrastructure Managers on suitable or available hypervisors. This could create vulnerable co-residency scenarios should the hypervisor become exploited or the security policies not be applied properly to the respective VNFs.



















