Managing Cellular IoT Security
Threats to the Enterprise
Service DoS attacks
These are like other DoS attacks but made with the intent of disabling business or national services and not specific devices. For example, such an attack can disable the logging service of an IoT device while leaving functionality intact to be used in the next stage of a multi-layered attack.
Enterprise cellular IoT
identity compromise
ToRPEDO attacks
ToRPEDO (TRacking via Paging mEssage DistributiOn) attacks allow hackers to determine the identity of the device and where it is located within a geographical region. Such attacks can even be used to identify the device owner. Hackers make repeated attempts to send multiple SMS messages or service requests to a device in a short period of time. They then sniff the paging message to determine the Temporary Mobile Subscriber Identity (TMSI) of a device and subsequently learn its location and even its International Mobile Subscriber Identity (IMSI). This, in turn, can reveal the device owner’s identity.
IMP4GT attacks
These attacks allow cybercriminals to impersonate devices or users by exploiting integrity protection flaws in the cellular connectivity protocol. The attack can be used for uplink and downlink impersonation according to the attacker’s objectives and opportunities enabled by flawed security policies on the network. Though somewhat complex to deploy and implement, this type of attack can modify the IP identities of each of the parties: the target device (uplink impersonation) or the network server identity (downlink impersonation). As a result, the attacker can then access any service on the network while assuming the victim’s identity. Alternatively, they may mimic the communications with the service of a legitimate service provider the target device may connect to.
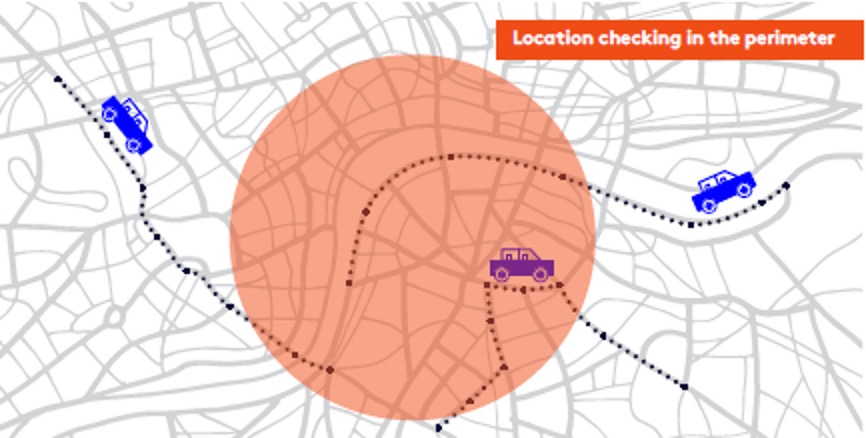
Figure 2: Location checking in action
Enterprise cellular IoT location data exposure
Location tracking
All cellular devices communicate with the network they are connected to. Among the data they transmit—and necessary for uninterrupted service—is the physical location of a device. By exploiting existing flaws in communication protocols like SS7 and Diameter, attackers can gain access to the location of a device. While not very significant in static cellular IoT deployment scenarios, such attacks can put at risk valuable assets transported in connected vehicles.
Location checking
Unlike location tracking, which follows a device around, location checking lets attackers know when a specific device enters a certain geographic location (see Figure 2, above). This can be, for example, a trigger as part of a wider attack to harm devices or business operations in a specific area.