Managing Cellular IoT Security
Threats to the Enterprise
Eavesdropping attacks enabled by data channel rerouting can put sensitive business data at risk. Data tampering can have even more significant repercussions, leading to massive disruptions in supply chains—or even put human lives at risk.
Using IoT devices as tools in an attack
IoT devices as a gateway
IoT devices themselves can be used to gain access to a company’s internal systems. Hackers exploit vulnerabilities within the device and use that device to get into the other zones in the networks of the company. This lets attackers effectively steal data, trade secrets and other critical information.
Enterprise cellular IoT
Denial of Service (DoS) attacks
IoT DDoS attacks
In addition to using IoT devices to gain access to data, attackers can employ them to launch Distributed Denial of Service (DDoS) attacks. These can shut down some or all aspects of operations. These attacks are an increasing problem for IoT devices, as attackers typically exploit devices that are poorly protected due to leaving security “holes” in the perimeter, such as factory default passwords.
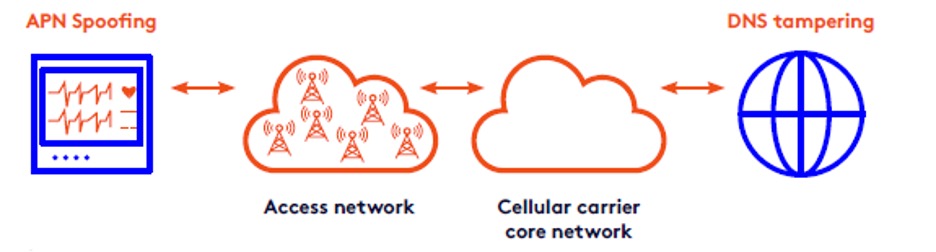
Figure 1: How a data channel rerouting attack works
Targeted DoS attacks
These attacks are designed to single out a specific connected device or a group of such devices and take it offline. This can be done by flooding the device with information that triggers a crash. Alternatively, fake cell towers and exploitation of SS7 network vulnerabilities can deny the device connectivity to the mobile network at the attacker’s will. These attacks can disconnect manufacturing and monitoring systems, and halt the production of electricity, all while preventing administrators from accessing their systems.
Non-targeted DoS attacks
These attacks aim to knock down everything on a network rather than disrupt the service of a specific device. While the attack method can be very similar to that of a targeted DoS attack, non-targeted DoS attacks are often executed by attackers aiming to disrupt an organization (or even a whole nation) impacting devices and services indiscriminately.
In cellular networks, such attacks are often launched by exploiting flaws in the cellular network’s connectivity protocols. These flaws enable attackers to impersonate the identity of another (legitimate) device connected to the service (using the above-mentioned IMP4GT attacks, for example), which in turn lets them flood the network to deny service to other endpoints.