Going Beyond the SOC
In DevOps, innovation and bug-fixing is an ongoing, 24/7 operation built on top of continuous integration and continuous delivery (CI/CD) systems. Modern CI/CD allows developers to focus on building and enables the smallest of teams to build market-defining products. Mundane and complex tasks are fully automated in CI/CD, and developers are required to emplace proactive testing for all features they roll out. This significantly reduces errors and bugs in the systems, which allows developers to focus on what matters most.
The traditional work of a SOC is pitting a dedicated team of humans against thousands of alerts. But premier technology companies have adopted a new model: trusted, well-documented, high-fidelity alerts get attention, but most alerts can be ignored because of automation. The most advanced cybersecurity platforms automatically send routine alerts to the infrastructure or application owner responsible for that particular area—whether it’s a firewall, an end user, an application or a server—along with a set of recommended responses. As Alex Maestretti (current CISO at Remily, former engineering manager at Netflix, where the SecOps team is SOCless) put it, this is what is meant by SOCless: decentralizing alert triage to system experts. The solution to alert fatigue isn’t more humans or more data, it's robust autonomous systems with decentralized processes.
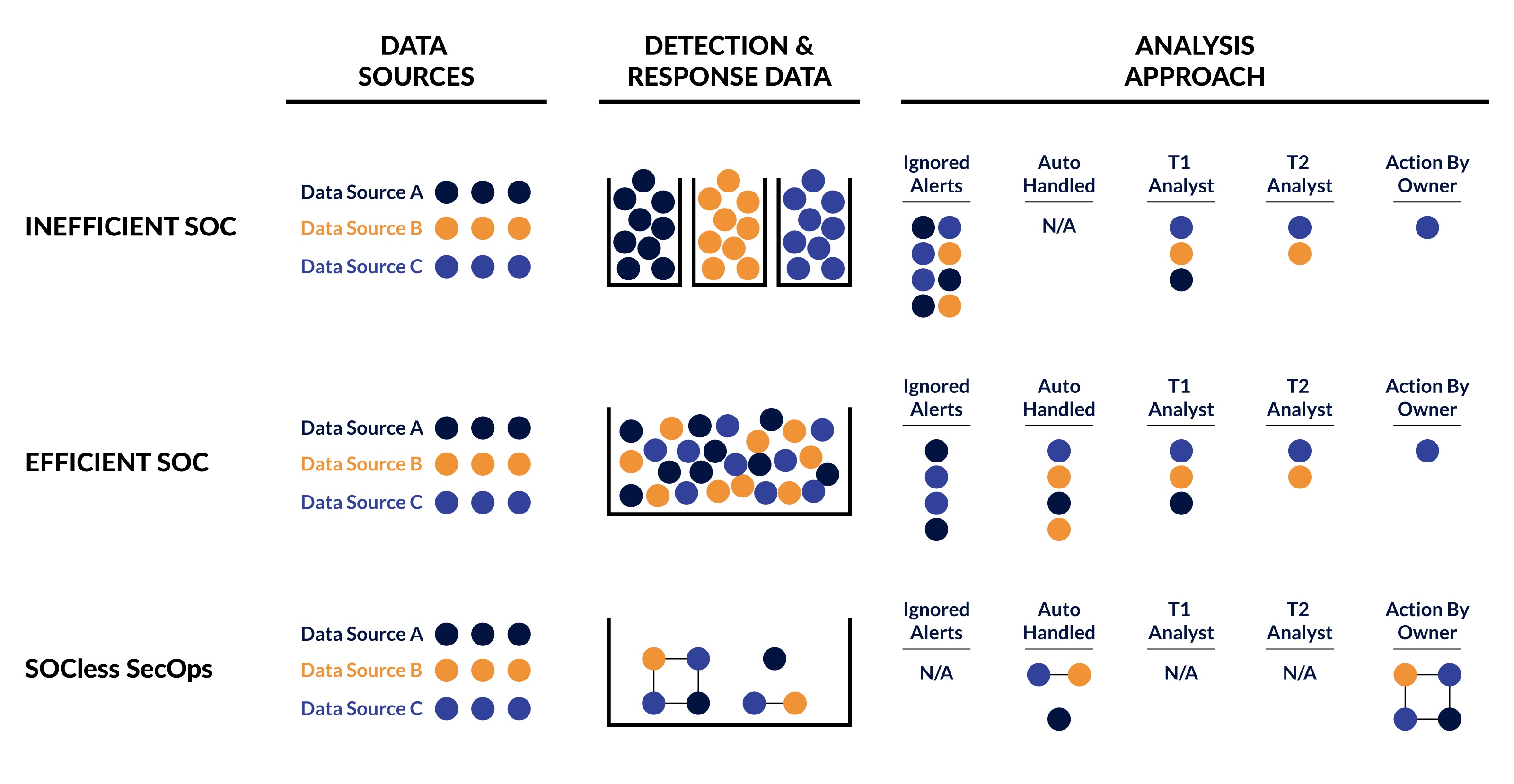
Figure 2: SOCless in practice compared to SOC-based approaches to SecOps
click to enlarge
Migrating to SOCLess
To make this SecOps model work, the security department needs people continuously contributing meaningful policy changes, detection strategies and playbooks, not staring at monitors looking for alerts. It takes work and commitment to get to that state, but if analysts are always monitoring alerts, they’ll never get ahead of the problem. To enable proactiveness, security teams need the CI/CD equivalent for security infrastructure.
The first requirement is to have core risk management controls with hygiene best practices easily applied. One prime example of this is the thorough implementation of zero trust; this not only improves your security posture but also reduces alerts and noise, thereby simplifying the data problem. The second requirement is a cybersecurity detection and response platform where strategies and playbooks can be rapidly deployed. Rapid deployment and configuration are paramount: the time from detection and response idea to production deployment should be as close to zero as possible. Any detection and response platform that supports this will be easy to use and have significant out-of-the-box content, including AI- and machine learning-based detections, because rules don’t cut it.
Going SOCless takes more than technology, however. It takes a committed team and reimagined processes—getting comfortable with significant automation, having infrastructure owners receive relevant alerts directly, and dedicating majority time to proactive security work. There will always be a need for people, however, and for many enterprises, augmenting internal personnel with a managed security service provider is a cost-effective way to stay proactive. An enterprise does need people to ensure that the right strategies are continuously deployed, and an MSSP with a co-managed deployment of a detection and response platform enables enterprises to scale up support as needed. Like enterprises have turned to the cloud for as-a-service offerings, they can turn to MSSPs for SOC-as-a-service offerings. This will aid many in completing the internal SOCless transition.
By taking a good look at distributed DevOps functions and mapping that to distributed security operations (SecOps), companies can start to get ahead of the hackers in terms of spotting and remediating complex attacks. It takes a real change in perception to pull it off, but many of the biggest and most advanced companies on the planet have already gone SOCless. Maybe it’s time every other company did, too.



















