Technology Can’t Save You from Cyberattacks
Market aggregators like managed security services providers (MSSPs) or value-added resellers (VARs) aren’t a strategy either. They may help sift through the deluge of security products, implement solutions, or assess existing cyber investments, but they can be costly relative to results, and all too often the heavy lifting falls on the buyer.
Never forget that, pre- or post-breach, all of the solutions we buy must be managed and maintained continuously. Defined resources—whether in-house or outsourced—need to be explicitly responsible for making sure that happens.
The path to cyber resilience
Successful security programs build on the basics using the three pillars of people, process, and technology. Organizations that look no further than technology will find they’ve invested in only one-third of a complete solution; without adding skilled resources and proven security protocols, even the best technology will leave them vulnerable to attack.
Unfortunately, the cost and complexity associated with cyber risk makes it hard for organizations to make the three pillars work in concert, but the newly emerging cybersecurity-as-a-service (CSaaS) trend marries them seamlessly—and affordably. CSaaS takes the guesswork, high costs, and high levels of difficulty out of the equation by using a holistic approach, proven technologies, and successful, repeatable best practices designed to scale.
Traditional providers mark up the technologies they sell and charge additional fees to install new software or remediate in the event of a breach, obscuring the total cost of any given solution. CSaaS bundles comprehensive offerings into all-in-one monthly subscriptions based on the buyer’s needs, so pricing is consistent and predictable month over month, even should an incident occur.
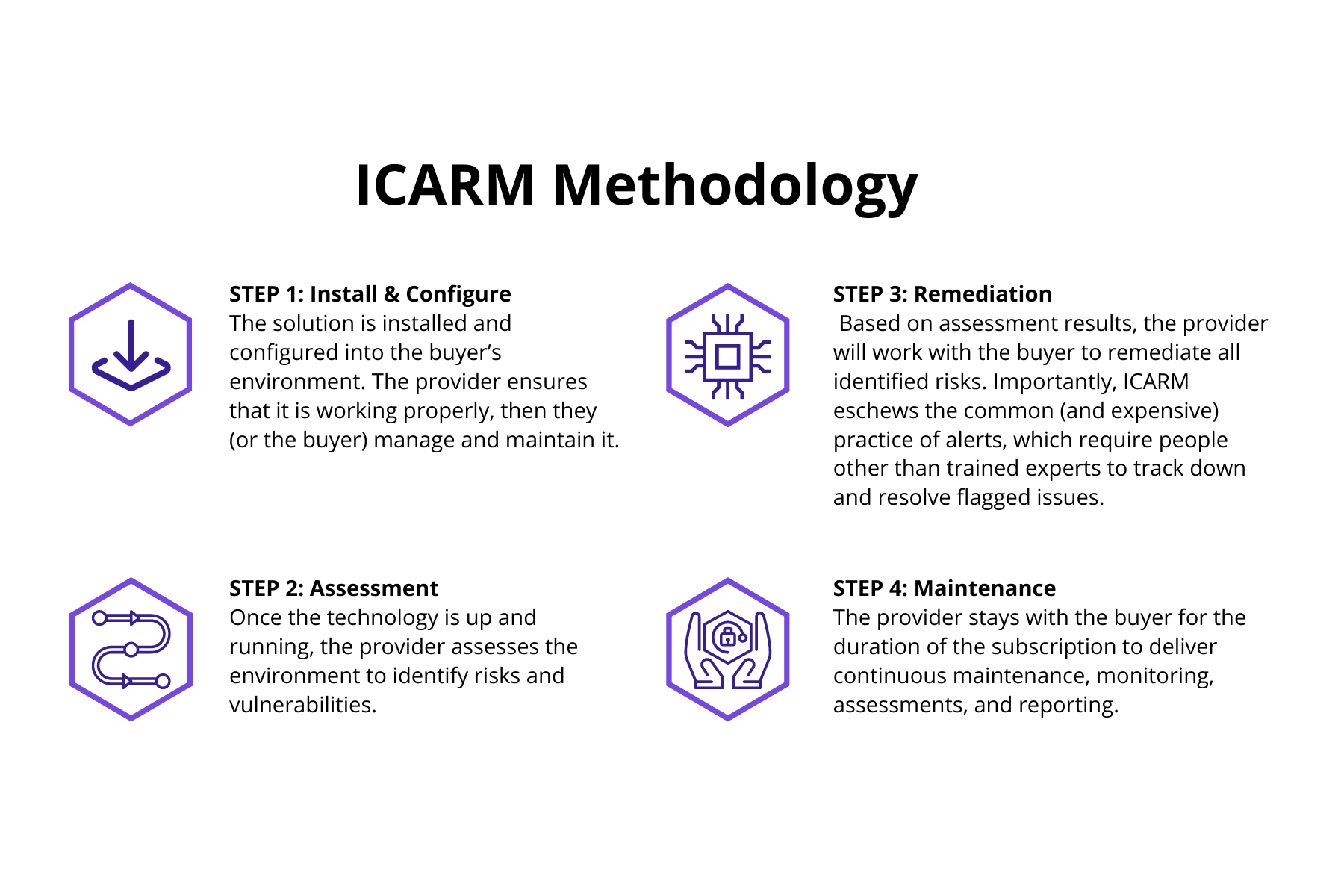
Figure 1: ICARM Methodology
click to
enlarge
Importantly, CSaaS makes formerly expensive solutions accessible and affordable for even the smallest organization, which traditional product companies cannot do. The subscription model allows CSaaS providers to deliver the same robust security enjoyed by large enterprises at price points friendly to startups and SMBs so they too can effectively combat rising threats. The ICARM method (for installation, configuration, assessment, remediation, and maintenance) enables them to realize quantifiable returns on their cyber investments. Figure 1 shows how it works, with the steps of the ICARM methodology explained.



















