A New Framework for Cybersecurity
Simply put, many organizations currently lack the tools and methodologies needed for identifying, prioritizing, and remediating the cybersecurity risks in their infrastructure.
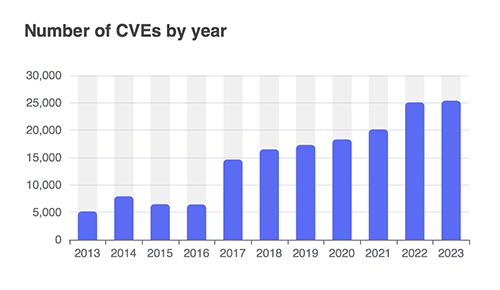
Figure 4: Number of new vulnerabilities (CVEs) reported annually.
Source: cvedetails.com
The CTEM Framework
In July 2022 security analysts at Gartner introduced a security approach or framework called Continuous Threat Exposure Management (CTEM). They identified the need for such an approach based on the issues outlined above – inadequate security testing regimes, lack of accurate risk-based prioritization, and lack of continuous assessment.
The CTEM process described by Gartner is a five-step cycle, which as the name suggests, should be carried out on a continuous basis so as to keep up with the dynamic nature of IT environments and threats. The steps to this process are:
Scoping: Define the boundaries of the IT environment that will be subject to threat exposure management. This typically includes the IT estate (data centers, office environments, cloud services, remote workers), but can extend further.
Discovery: Identify all the assets within scope. This includes device and software configurations, vulnerabilities, security controls, connectivity, and asset value. The process requires a system-wide approach as opposed to a collection of siloed results from vulnerability scans, audits, and pen tests.
Prioritization: The goal of this phase is to identify the exposures most likely to be exploited and their potential impact on the organization. In short, the exposures must be measured in terms of likelihood and impact. This equates to risk-based prioritization.
Validation: This is a testing phase where the exploitability of exposures is confirmed along with potential impact on assets. This goes beyond determining whether a given system or control can be compromised. It includes how the compromise could be leveraged (e.g., lateral movement) to gain access to high-value assets. An exploitable system may not pose a high risk if an attacker cannot leverage that system to do significant damage.
Mobilization: This is the remediation phase. The previous four steps reveal a risk-prioritized list of exposures, including the details of what systems are involved and the specific attack paths an attacker would follow to leverage each exposure. This provides not only the information needed to determine what issues need to be addressed most urgently, but also the most efficient and effective ways to achieve remediation.
Like security frameworks we have seen before, this looks great on paper, but implementation is where things get difficult. CTEM is a framework/process and not a tool. However, without effective tools that address the shortcomings in how exposure management is done today, CTEM is unlikely to make a significant impact on reducing cyber risk.
In a previous Pipeline article we described the emerging use of reasoning-based AI and digital twinning technologies in cybersecurity. Reasoning-based AI attack path simulation applied holistically to a virtual cyber twin of the IT environment overcomes many of the barriers to implementing the CTEM framework. These technologies are not “CTEM in a box,” but they do provide the means for organizations to implement the CTEM framework and achieve the 3X risk reduction that Gartner forecasts.