A New Framework for Cybersecurity
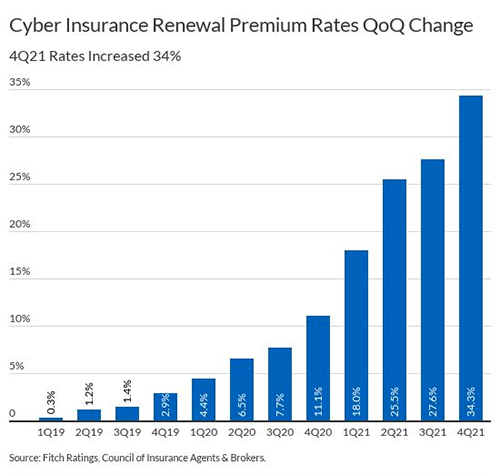
Figure 2: Quarterly change in premiums for cyber insurance
"Left of Bang" Cybersecurity Problems
There is strong evidence that organizations are falling behind in their efforts to ensure their security controls are up to date and working as needed. A look at how this is done today reveals why. Let’s take a look at the major tools of the trade in this area.
Figure 3: Time to identify and contain breaches.
Source: IBM Cost of Data Breach Report 2023
First, we have compliance audits. These audits are infrequent (annual, quarterly at best) and are basically paper checklists. They do not actually test if controls are working as needed. And because they are infrequent, they quickly become out of date due to the dynamic nature of IT environments. Security professionals have long known that compliance ≠ security.
The next set of tools for ensuring the effectiveness of security controls is penetration testing in various forms. These include manual or semi-automated pen tests, red team-blue team exercises, and fully automated breach and attack simulation (BAS). A primary impediment to effective testing, however, is the impact a pen test can have on a live production network. To avoid such impacts, the tests are often limited in scope and frequency. Some tests may be restricted to only lab environments. The other issue is the tests typically focus on a specific control (such as firewall, or endpoint security). This approach does not measure overall risk to the IT system. It tells you if something is not working but does not measure the potential impact (risk) of the exposure. Testing techniques in their various forms lack system-wide coverage, are scope-limited, and are often too infrequent to keep up with changing IT environments.
The final tool in the prevention tool bag is vulnerability management and prioritization. As you can see in (Figure 4 on next page) about 25,000 new vulnerabilities are found annually.
Organizations regularly scan their endpoints, servers, network gear, and applications to find which vulnerabilities are present in their environment, and there are almost always many more identified than can be addressed. The list must be prioritized down