A New Framework for Cybersecurity
 It is no secret that current approaches to cyber defense are failing to stem the tide of successful attacks on enterprises of all sizes. An approach to reducing risk called Continuous Threat
Exposure Management (CTEM) is emerging that Gartner predicts will reduce the chances of system breaches by a factor of three. This article explains the CTEM process, why it is needed, and how
businesses can implement it.
It is no secret that current approaches to cyber defense are failing to stem the tide of successful attacks on enterprises of all sizes. An approach to reducing risk called Continuous Threat
Exposure Management (CTEM) is emerging that Gartner predicts will reduce the chances of system breaches by a factor of three. This article explains the CTEM process, why it is needed, and how
businesses can implement it.
Current Cybersecurity Basics
But before getting into the details of CTEM let us review some basics of how organizations typically do their cybersecurity and examine why they all too often fail to prevent security breaches.
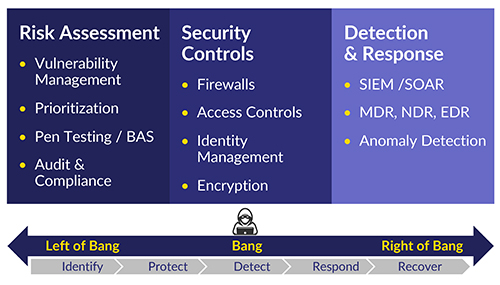
There are essentially three components to any cybersecurity system. The central component is cybersecurity controls. Simply put, the purpose of controls is to establish and enforce the rules governing who may access what and when within an IT system. There are hundreds if not thousands of products on the market that provide these controls. Generally, however, they include (a) firewalls – of which there are many types; (b) identity and access management tools – Active Directory for example; and (c) encryption – for both data at rest and in motion.
Putting these controls in place is not a matter of “set it and forget it.” That brings us to the other two components of the cybersecurity system. The first is a system and methodology for ensuring the controls are deployed, operational, and working as intended. The tools and methods for this include periodic audits and compliance verification, vulnerability and patch management, and penetration testing.
The last component is best described as monitoring, prevention, detection, and response. In spite of best efforts to deploy strong security controls and ensure the controls are up to date and working well, attacks continue to occur, and some will breach the security defenses. To prevent or limit damage from successful attacks we need systems to detect and respond to them. Tools for intrusion prevention, detection and response include Security and Information Event Management (SIEM); Security Orchestration, Automation and Response (SOAR); and Detection and Response (EDR, NDR, XDR).
The foregoing components are encapsulated in Figure 1 below. From a timeline perspective, they comprise the activities designed to prevent a successful attack (“Left of Bang”) and activities that take place after a successful attack (“Right of Bang”).
Where Cybersecurity Fails
Yet despite increased organizational investments in cybersecurity products, services, and personnel, cybersecurity risk is on the rise, and the frequency and cost of successful attacks are increasing.
This increased risk is evidenced by the rising cost of cyber insurance (see Figure 2, on next page). Premiums are not only rising; carriers are also lowering payouts and coverage.
So why is risk rising so dramatically? Is it due to failures in controls, prevention, or detection and response? All the above?
In some cases, controls are at fault. A common control gap, for example, is a failure to implement multi-factor authentication. However, this and other control gaps (such as weak privileged access management) are usually not difficult to identify and address. In fact, such controls are becoming a requirement for obtaining cyber insurance. As organizations implement stronger controls, we would expect risk to decline, not rise.
Nor does the data regarding detection and response explain why risk is increasing. In fact, we have seen some recent improvements (reductions) in mean time to detect (MTTD) and mean time to respond (MTTR). The 2023 data breach report from IBM shows only minor changes over the past several years, including some decline


















