Averting Modern Telecom Scams: Fraud Prevention in a VoIP World
Many service providers still rely on inefficient and rudimentary practices for fighting fraud
Service providers that incorporate fraud protection features into their offerings and maintain a knowledgeable support staff are, in fact, able to differentiate their PBX service offerings. In some markets PBX customers expect their service providers to proactively prevent fraud and cover any fraud-based losses if they occur.
Here are the more common scams to look out for:
- PBX/voicemail hacking and call-transfer schemes, like the Massachusetts case in which fraudsters gained access to an enterprise PBX or voicemail system (or, in some cases, the softswitch in the service-provider network, albeit indirectly) for the purpose of making free long-distance or international calls. In more sophisticated versions of the scam, rogue service providers “resell” the services to their own subscribers or place calls to their own premium numbers to collect termination fees (revenue-share fraud);
- Traffic-pumping schemes, in which rogue carriers strike traffic-steering deals with conferencing services or adult entertainment services, or in which subscribers are duped into placing calls to premium-rate services;
- Bypass fraud, in which SIM boxes (GSM gateways) are used to circumvent standard network interconnections and avoid the normal payment systems for international mobile calls. In one popular mobile calling scheme, fraudsters sell inexpensive overseas calling cards to expatriates and illegally route international calls across the Internet or a VoIP network to a GSM gateway for handoff to a local mobile-service provider. By making internationally originated calls appear as on-net mobile-to-mobile calls, these schemes rob the home mobile operator of standard international connect fees while creating QoS and spectrum management issues. A rash of SIM-boxing schemes has made international headlines over the past several years; in Ghana, for example, investigators have recently broken up dozens of scams, most involving hundreds of SIM cards, which were believed to have cheated local mobile operators out of millions in monthly service fees.
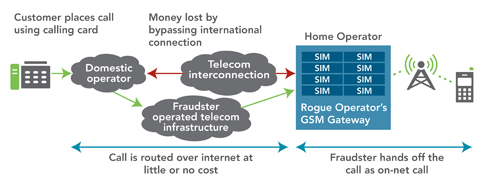
Figure 1 - International calls are disguised as on-net calls in a typical SIM boxing scheme
Conventional Techniques for Combating Telecommunications Fraud Fall Short
Many service providers still rely on inefficient and rudimentary practices for fighting fraud, including:
- Call blocking, in which the provider simply rejects calls to countries with high incidences of fraud (Cuba, Somalia, Sierra Leone), forfeiting legitimate international calling revenues;
- Third-party routing, in which the provider routes calls to high fraud countries through intermediary “validation service” operators, who verify call legitimacy at additional expense;
- Call Detail Records (CDR) analysis, in which switch call detail records are scrutinized for unusual calling patterns. While basic CDR analysis can help identify or isolate certain types of service theft, it typically cannot be used to detect or prevent acts of fraud in real-time (as the aforementioned roaming-fraud example illustrates); service providers can lose millions before a threat is discovered and contained. Worse still, conventional CDR analysis tools aren’t capable of detecting contemporary threats like IP reconnaissance scans, which hackers often use to identify and exploit security weaknesses in VoIP networks.



















