By: Tim McElligott
The greatest logical thinker of our time said, “Logic is the beginning of wisdom, not the end.” That the words were uttered by a fictional character known the sci-fi world over as Mr. Spock
should not diminish their significance; after all, they were written by a human, perhaps even Leonard Nimoy himself. But here in the 21st century, on earth, in a world of evolving computing
technology, logic is often the beginning of something else: stifling complexity. Humans think of themselves as logical beings, but they are still proving to be much more adept at the
physical…
» read this article
By: Becky Bracken
Is it mere coincidence that Chinese gear manufacturers ZTE and Huawei have become the focal point of what essentially looks to be a public relations feeding frenzy for members of the U.S. House
Intelligence Committee at the very same time election season has reached its full-fevered, sweaty, smelly peak?Politicians running for everything from local city councils to even the most
politicized, publicized national contests regularly, angrily demand “fairer” trade with China as a tool to create jobs and bolster a struggling economy…
» read this article
By: Paul Kenyon
While many readers will be familiar with the Department of Homeland Security in the U.S., there are similar security initiatives being planned, or already under way, elsewhere in the world. In
Australia, for example, under the guidance of Prime Minister Julia Gillard and her federal team, the government is carving out something of a name for itself in the IT security arena. This
development is somewhat surprising considering Australia’s relative youth and the fact that the country has around 22 million citizens — big enough to make its weight felt in international terms,
but small enough to be flexible in the modern world of IT matters…
» read this article
By: Alex Hoffman
Telecommunications fraud is a significant concern for communications service providers. It robs carriers of revenues, consumes valuable network resources without remuneration and leads to
customer disputes and churn. A 2011 Communications Fraud Control Association (CFCA) survey estimated global telecommunications fraud loss at $40.1 billion (USD), or nearly 2 percent of worldwide
telecom revenues. Next-Gen Networks Are Susceptible to a Myriad of Scams Today’s telecom networks and services are susceptible to many different types of fraudulent activity…
» read this article
By: Jesse Cryderman
Anyone with a finger on the pulse of telecommunications will tell you that a seismic shift is occurring, and it’s bigger than 4G or VoLTE. This change will predominantly occur over 2G, WiMAX
and Wi-Fi, and it has very little to do with customer experience management (CEM). That’s because the connected future belongs to machines, and machine-to-machine communications (M2M) will
eventually outnumber human connections by a substantial margin. The applications for M2M are limitless: from vending machines to healthcare devices to home appliances and public safety systems,
nearly everything that can benefit from connectivity will…
» read this article
By: Patrick Sweeney
Protection and performance should go hand in hand in terms of data and network security. However, until the introduction of Next-Generation Firewalls (NGFWs) organizations often had to
compromise data throughput and productivity for security. But while NGFWs are good news for business, many organizations are unaware that they have “old” firewalls, ones that are barriers to
productivity but not, unfortunately, barriers to the latest security threats. A Quick History of Firewalls First-generation firewalls of the 1980s provided packet filtering based upon criteria such
as port, protocol and MAC/IP address, and operated at layers 2 and 3 of the OSI model…
» read this article
By: Jesse Cryderman
Few telecommunications systems are as important as the emergency response platform that effects everyone in the U.S., 9-1-1. This analog system is comprised of public-safety answering points
(PSAPs) and relies on telco billing-system data to provide location information for first responders. The faster this data can be pulled and distributed to the appropriate teams, the better: swift
palliative care following a serious injury improves survival rates, and fires that are suppressed early cause less personal and property damage…
» read this article
By: Becky Bracken
The loyalty of your customer, your reputation, your bottom line — all can be destroyed in a matter of seconds by network security vulnerabilities. Security breaches like the all-too-common
distributed denial-of-service (DDoS) attacks can overwhelm networks with fraudulent traffic and lead to service disruption. Thefts of large swaths of customer data are a real, everyday looming
threat and could open up operators to extensive litigation. And worse, interception and penetration of networks have never been easier…
» read this article
By: Becky Bracken
It’s a natural evolution, really. Now that we’ve unlocked the key to flinging data all over the place — from the cloud to mobile devices and back again — the next question, naturally, is how to
keep that data secure while it’s being flung far and wide. Particularly in North America, the mobile-enabled workforce is taking shape. It’s also what’s driving the BYOD frenzy. Almost every
job can be made that much easier with a mobile handheld computer — and everyone has their own brand of choice…
» read this article
By: Tim Young
Nowhere has the “walled garden” of old been less successful than in the mobile sphere. Smartphones, tablets and other mobile devices are now little traveling bazaars of widely varied apps
routinely accessing device information of varying sensitivity. Nielsen reported in May that the average smartphone in the U.S. contains 41 apps, and Android and iOS apps downloaded to date both
reach well into the tens of billions. It’s a wonderful thing, for the most part. I know that I would be pretty bored with my iPhone if its applications were limited to those supplied by, or even
developed by, my CSP and device manufacturer…
» read this article
By: Jesse Cryderman
As third-quarter reports rolled in, earnings among tier 1 CSPs in the U.S. proved a mixed bag, but one fact became clear: shared data plans have provided a big boost to bottom lines. AT&T
added 200,000 fewer subs than expected but reported the strongest wireless ARPU growth in six quarters. And though wireless service revenues as a whole crept up less than 5 percent, the company
reported a spike in mobile data revenue of more than 18 percent, or a full $1 billion more than in the third quarter of last year…
» read this article
By: Tim Young - do not use (default)
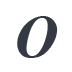
rdinarily, I
like to begin these monthly letters with a quote. Something light and pithy to sum up a given issue's theme. It might be a little funny or maybe vaguely inspiring, but it's always
designed to work with the central topic of the issue while accurately representing our editorial take on the topic…
» read this article
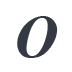 rdinarily, I
like to begin these monthly letters with a quote. Something light and pithy to sum up a given issue's theme. It might be a little funny or maybe vaguely inspiring, but it's always
designed to work with the central topic of the issue while accurately representing our editorial take on the topic…
rdinarily, I
like to begin these monthly letters with a quote. Something light and pithy to sum up a given issue's theme. It might be a little funny or maybe vaguely inspiring, but it's always
designed to work with the central topic of the issue while accurately representing our editorial take on the topic…
















