Next Generation Cloud Security
If the corporate remote user's desktop is compromised, the VPN can force disconnect and prevent the attack based upon IPS, bad authentication, host inspection, and others. If the resource is
internal and not reachable via the Internet, disconnecting from the VPN will prevent the user (and attacker) from accessing the desired source.
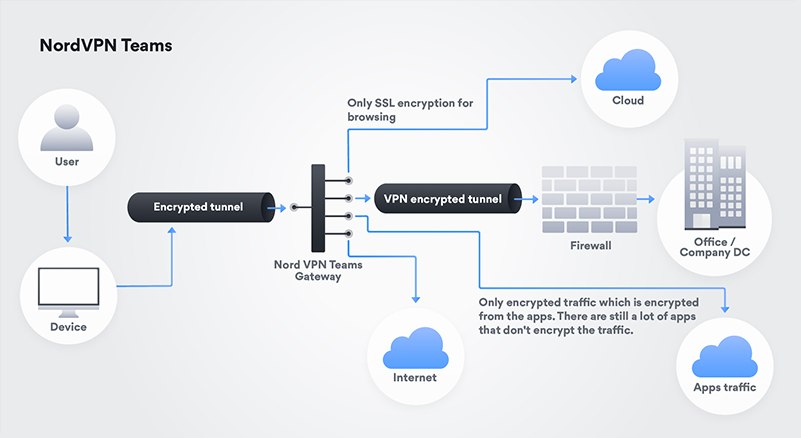
Figure 2: Nord VPN split
(click to enlarge)
At the start of the pandemic, companies and their employees had been thrust into a remote working environment rather suddenly, with many organizations’ remote networking capabilities still not as
shielded as their on-site IT infrastructures. This rapid shift has left many unsecured gaps that malicious actors are looking to exploit for financial gain — or to simply disrupt usual
operations. The priority therefore is to secure endpoints and implement stronger authentication protocols for the cloud and other off-premises networks.
By passing the traffic via NordVPN Teams Gateway, users can change settings from ‘’allow all’’ to ‘’deny all’’ and only allow users with a fixed IP address to reach the
desired source. This works as an additional security layer, which hides a firewall from the Internet, narrowing down the area of attack.
Patching remote workers
While most enterprises want to prioritize patching and endpoint hardening, they are inhibited by the pace of digital transformation and modern workforce evolution. Businesses often cite the
difficulty in patching systems belonging to mobile employees, remote offices, inefficient patch testing, lack of visibility into endpoints, and insufficient staffing in SecOps and IT operations
to successfully do so.
As many businesses shifted to fully remote staff during the pandemic, they have fallen behind in patch management. Organizations are finding it tricky to manage attack surfaces that aren’t hidden
behind corporate Wi-Fi firewalls and many employees don’t even have their corporate devices at home currently.
When creating a remote work policy, organizations must consider what they want to do in relation to split tunneling. Businesses need to understand the architectural decisions that go into
implementation considerations and clearly understand the impact of these outcomes. One size does not fit all, and architects and engineers need to understand business needs before making
technical decisions.