Next Generation Cloud Security
Users that understand this technology appreciate the privacy and enhanced performance through improved routing paths.
One of the most effective protections an organization can implement is a strong network segmentation. Remote users’ access should be limited to only the systems that are required to perform their
job functions. Restrictions should be in place to segment your network to prevent unlimited network access for remote users. Segmenting VPN connections to access only the required systems is
paramount in creating a strong security barrier.Organizations can also minimize unauthorized access with a fixed IP method. This way they could reduce the risk of IP sharing when many devices use the same IP address. Companies therefore have a greater chance to protect themselves from vulnerabilities by changing their firewalls to only allow certain IP addresses on their whitelist. This hides the firewalls from the public.
Split tunneling vs. NordVPN Teams gateway
With increased traffic due to remote work and with a need to relocate to remote settings quickly, many companies have had to sacrifice security over speed and performance — elevating traffic using split tunneling. Using a business Virtual Private Network (VPN) for remote access involves what and how much data to send down the tunnel. When creating a VPN, network engineers have an option to enable “split-tunneling,” which sets a determination of what data traverses the VPN.Enabling split tunneling reduces traffic on corporate networks, increases speed through reduced latency for specific tasks, and grants privacy to end users. These key capabilities primarily reduce traffic on internal networks, with most organizations switching to split tunneling when they set up their VPNs. Users that understand this technology appreciate the privacy and enhanced performance through improved routing paths.
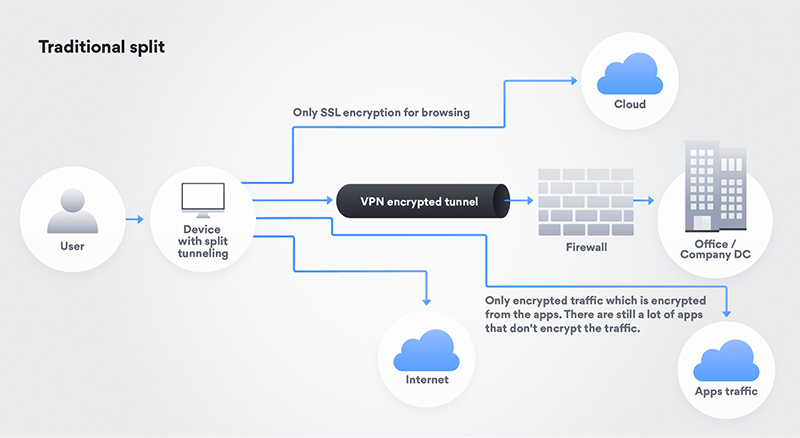
Figure 1: Traditional split
(click to
enlarge)
The core goal of providing split tunneling capabilities is simply to give your employees the ability to perform work and Internet functions from the Internet directly. This connectivity gives
your users the fastest capability to do their work using the sources that have the fastest network connectivity. Remember, security is an option if you deploy split tunneling.
As seen in the graphic above, the (remote) user connects their laptop to the VPN. Split tunnel method and policy then help to regulate what a user can access and how the user can reach the desired target. In other words, a company sets up subnets that are "inside VPN." All other traffic goes directly from the user to the Internet without a VPN.
As seen in the graphic above, the (remote) user connects their laptop to the VPN. Split tunnel method and policy then help to regulate what a user can access and how the user can reach the desired target. In other words, a company sets up subnets that are "inside VPN." All other traffic goes directly from the user to the Internet without a VPN.