Ransomware Defense: Cutting the Kill Chain
The IMI offers the following benefits:
- No more automation anxiety: The IMI is an environment where staff can build their automation skills, without worrying whether they’ll break the production network.
- No more outdated systems: The IMI is where staff can build end-to-end pipelines for automated patching, so their systems are always up to date.
- No more collateral damage: The IMI incorporates zero trust security and segmentation. If an attack slips through the cracks, it can’t spread beyond the entry point.
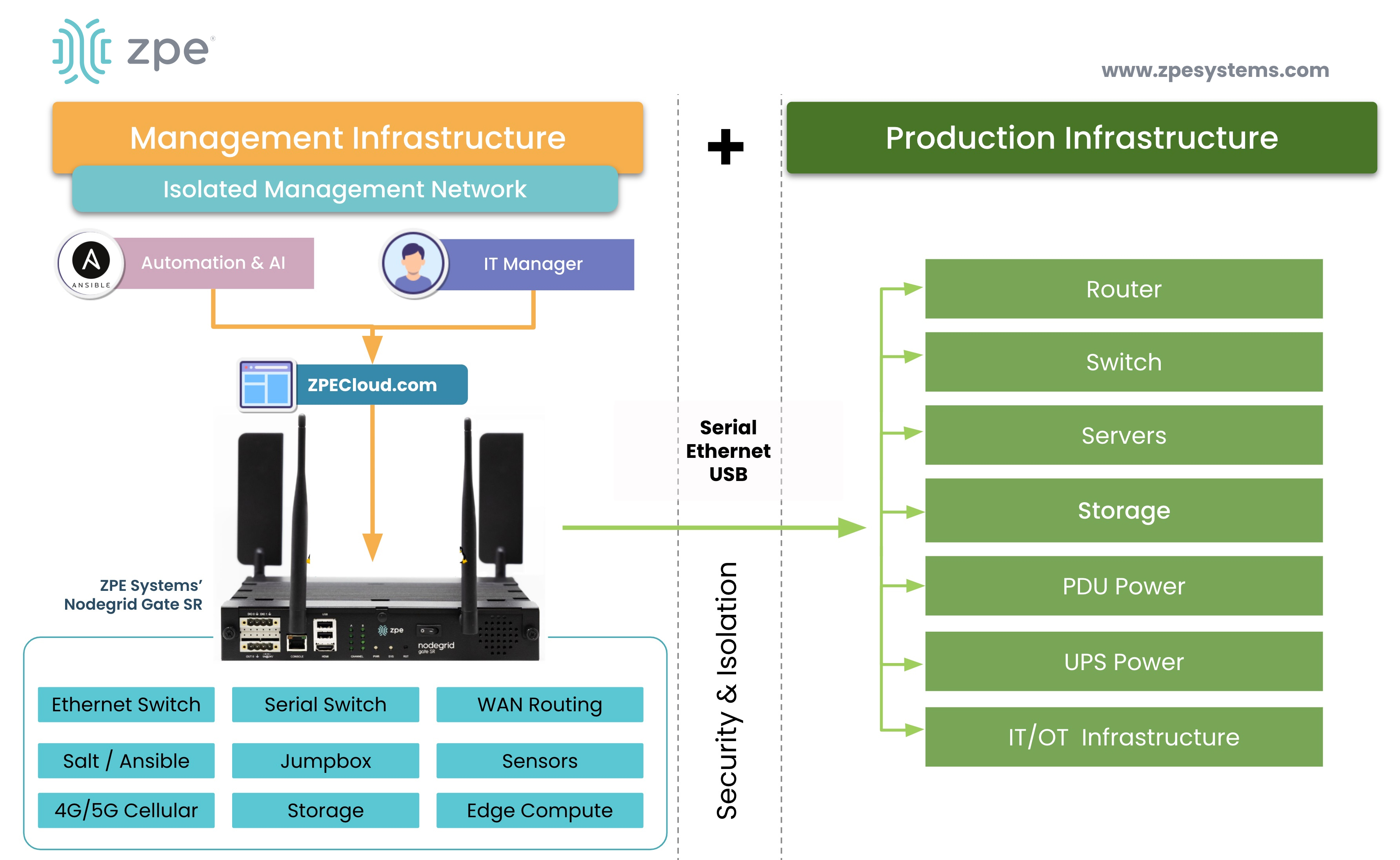
Figure 4: The Isolated Management Infrastructure (IMI) creates a management network that is fully separate from the production infrastructure.
click to enlarge
IMI addresses both ransomware attack vectors
Implementing an IMI is crucial to addressing both ransomware attack vectors. It offers a safe environment for teams to experiment with implementing new cybersecurity products or defense strategies. But more importantly, the IMI is a secret weapon that allows organizations to fight back against ransomware and recover quickly.
Closing the Social Engineering Attack Vector
Human errors and social engineering trigger significant ransomware attacks. Creating accounts and opening malicious files on non-segmented, in-band management networks results in widespread infrastructure damage and millions in financial losses. But the IMI closes this attack vector, by providing administrators with an environment that’s completely separate from production systems. This allows them to experiment with new training and tools, develop their automation skills, and gradually implement NetDevOps practices. The IMI helps to ensure that any change, whether it be creating a new account or installing a file, goes through an approval process. This drastically increases the chances of cutting the kill chain before the attack can even begin.
Strengthening Weak Systems
Attackers find it easy to fracture traditional systems, because they’re usually outdated and offer feeble options for recovery. But with an IMI, they get to implement both defensive and offensive tactics. For defense, the IMI lets them safely test automation workflows to ensure system integrity and achieve a lights-out approach that automatically installs the latest patches. If an attack does breach their defenses, teams get to fight back using dedicated management access to every piece of infrastructure. They can deploy what Gartner calls an Isolated Recovery Environment (IRE). Using the IMI’s fully isolated management interfaces, teams can use the IRE to take affected systems offline, wipe configurations/devices clean, and restore systems without risking reinfection.
Make sure you can cut the ransomware kill chain
Despite thousands of modern cybersecurity products, combating ransomware depends on an organization’s ability to avoid social engineering exploits and system weaknesses. Recovery is now just as important as prevention. This involves implementing adequate defenses in the form of automated patching, and also having the ability to fight back against attacks by using NetDevOps and segmentation. The critical step any organization can take right now is to implement an Isolated Management Infrastructure (IMI), which is a best practice that has been in use by Big Tech for nearly a decade.
To help organizations get started, ZPE Systems has released a comprehensive Network Automation Blueprint that outlines how to build the IMI. Download this blueprint to gain valuable insights and contact ZPE Systems for consultation on deploying IMI.



















