Ransomware Defense: Cutting the Kill Chain
Ransomware Threat Vector 2: Weak Systems
Once a breach is successful, it spreads at machine speed to discover and exploit weaknesses within the system itself. The MGM attack is a perfect example of this. The adversary, having gained elevated Okta privileges, deployed a ransomware “vending machine.” This began to automatically spit out scripts to every server and encrypt critical applications within minutes. The casino giant was left with no option other than to shut down revenue-generating services.
|
|
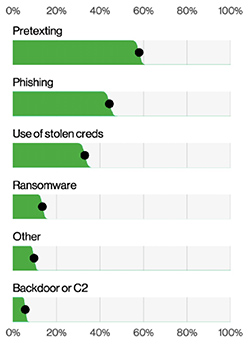
Figure 3: Action varieties in Social Engineering incidents. |
- Unpatched systems: A joint study from 2022 showed that 76% of vulnerabilities still being exploited were discovered between 2010 and 2019. Attackers know that admins are reluctant to update systems due to the potential to cause outages, which means the landscape is rife with outdated and vulnerable targets.
- In-band management: Many organizations use a management network that relies on their production network. When attacks occur, this makes it impossible to take systems offline to sanitize, rebuild, and restore. If attackers have persisted in this network for any length of time, it’s likely that they’ve also compromised backups, making it impossible to recover quickly.
Why it’s difficult to cut the ransomware kill chain
There are several ways organizations can reinforce their defenses against ransomware. These address the processes and systemic challenges described in the threat vectors above, and include:
- More training: Extensive training empowers IT staff to more effectively identify, detect, and prevent cyber exploits, such as phishing/vishing and malicious emails.
- NetDevOps automation: NetDevOps involves integrating software development lifecycle practices into IT operations. Rather than IT staff making changes directly to systems, this approach mandates approvals from a secondary party before changes are deployed through an automation framework.
- Frequent patching: Regular system patching ensures organizations are protected from novel malware and CVEs (Common Vulnerabilities and Exploits).
- Segmentation and Zero Trust Security: Network segmentation, in the form of nano- or even pico-segmentation, reduces the attack surface as well as minimizes collateral damage. This involves segmenting user traffic and isolating management interfaces.
Every IT team can benefit from additional training, rigorous system patching, and comprehensive segmentation and zero trust measures. But, regardless of how prescriptive or precise their tactics may be, there’s a significant gap to overcome: teams simply don’t know where or how to start.
For instance, days before the MGM attack, Okta published an article outlining tactics to detect and prevent cross-tenant impersonation (the kind of attack that affected MGM). Even if staff had read up on the prescriptive, low-level approaches described in the article, they would still need to answer questions, like:
- In what environment do we implement these changes?
- How can we be sure that our changes won’t break anything?
- If an attack is successful, can we stop it? How fast? And what will it cost?
As previously mentioned, cybersecurity products are one critical component to combating attacks. But the other component is an organization’s ability to recover. Due to recent ransomware incidents, CISA, the FBI, and NetDevOps practitioners have described isolation as the key to combating ransomware.
How Isolation cuts the ransomware kill chain
In response to global vulnerabilities related to open management ports, CISA issued a binding operational directive that mandates organizations to establish an Isolated Management Infrastructure (IMI). As shown in Figure 4 on next page), the IMI fully



















