Ransomware Defense: Cutting the Kill Chain
By: Koroush Saraf - Advisor, Zerotouch.ai

Ransomware attacks plague organizations with major disruptions and financial losses. Gartner has gone so far as to describe ransomware as the modern-day disaster, with a Sophos survey showing that over 70% of affected organizations require more than two weeks to fully recover from an attack. Recent high-profile breaches on organizations like MGM and Caesars, as well as the thousands of organizations using the MOVEit protocol, have underscored the resilience and adaptability of threats despite there being thousands of modern cybersecurity products in use. Although security products are vital to protecting systems, the crux of the issue is rooted in what cybersecurity expert John Kindervag dubs the "chewy center" of the network – the people who operate IT.
Ransomware Threat Vector 1: Human Weakness & Social Engineering
Humans are the weakest link in any ransomware defense strategy. This is why they are the prime target for savvy attackers. Even the most keen-eyed administrators and network engineers can be tricked into opening a malicious file, clicking a deceptive link, or like in MGM’s case, creating an admin account for a seemingly real user. Ransomware groups leverage an organization’s trusted users to perform these minor actions, which then kick off the rest of the attack.
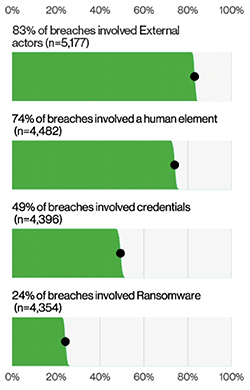
|

|
|
| Figure 1: Select key enumerations. |
Figure 2: Threat actor motives in breaches. |
Recent high-profile attacks prove how simple and effective it can be to exploit humans through social engineering:
- MGM attack: In September 2023, adversaries used “vishing” — a form of phishing over the phone — to convince an MGM staff member to create an administrator account for the attacker. This set in motion the entire kill chain, with the compromised account being used to create additional accounts, propagate the attack, and ultimately force MGM to shut down revenue-generating operations.
- RagnarLocker attack: In September and October 2023, cybercriminal group RagnarLocker used BEC to attack many organizations. Using a form of email stuffing, they tricked IT staff into opening seemingly legitimate files that would then encrypt systems for ransom. This affected critical operations for many organizations and their customers.To make this vector even more enticing,



















