Closing the Top Five Cybersecurity Gaps
Automation infrastructure: This layer is key to reducing anxiety around automation. This is a truly independent infrastructure that is connected to the production infrastructure in an out-of-band fashion. Customers call this the double-ring network (see Figure 3 below). This layer often uses a combination of serial console and Ethernet connections, along with staging jump boxes, local storage, TFTP source of truth, and version control systems. This layer is critical to automating diverse security products to work together, as it provides a safety net for teams to roll back to golden configurations in case of mistakes. In simple words, this automation infrastructure layer is able to destroy and rebuild the production network safely, so teams don’t have to worry about breaking any systems. It’s similar to having an IT person troubleshoot a locked-up device by typing commands in the console port to rebuild the device, but without any human interaction.
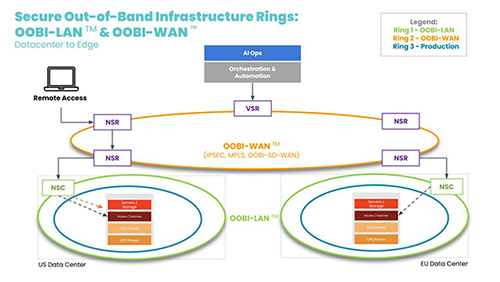
Figure 3: Dedicated automation network best practice known as double-ring architecture
click to enlarge
Orchestration and automation systems: This is where the desired outcome and playbooks are sourced from. The key is that the orchestration reaches the production systems through the independent out-of-band network to achieve the desired outcome.
AI Ops infrastructure: This layer receives rich information from observability platforms to make reactive and predictive decisions at scale. Using machine learning and artificial
intelligence, this layer learns the network’s normal behaviors and pushes changes through the orchestration and automation layer.
This blueprint is the reference architecture validated to successfully implement hyperautomation, as well as meet the Open Networking User Group (ONUG) Orchestration and Automation recommendations. This blueprint gives you the necessary layers to confidently implement a holistic cybersecurity approach and outlines the practical steps required to overcome the gaps described above.
Fight ransomware with the network automation blueprint, open cybersecurity platform, and OOBI-WAN™
A single-vendor cybersecurity strategy is no longer adequate to combat increasing cyber threats and ransomware. Organizations must reduce the attack surface and close gaps using a diverse fabric of security solutions. This requires an automation infrastructure to remove the anxiety from pushing upgrades and patches. A vendor-neutral, open cybersecurity platform also allows the best picks of security products to be positioned where needed. When automation infrastructure is independent of production infrastructure (out-of-band), IT teams can safely recover from errors, much like having a network-wide ‘undo’ button. This unique combination of automation infrastructure, open cybersecurity platform, and secure out-of-band enables teams to:
- Quickly patch infrastructure without fear of causing breakages and unscheduled downtime, using CI/CD pipelines to rebuild production at any time regardless of human resources (see this auto-upgrade/downgrade example of Fortinet firewalls here)
- Simplify the deployment of the necessary, multi-vendor security stack from datacenter to edge, by easily deploying vulnerability scanning from Vendor A, NGFWs from Vendor B, and experience monitoring from Vendor C
- Protect management portals and reduce the attack surface, by restricting interfaces and remote desktops to a private and secure out-of-band infrastructure (OOBI-WAN™) network
The network automation blueprint helps organizations close these gaps and achieve holistic cybersecurity, by explaining these techniques in detail. Download the complete blueprint from ZPE Systems.


















