The Cyber Security Remediation Bottleneck
Automated Remediation – A Network Immune System
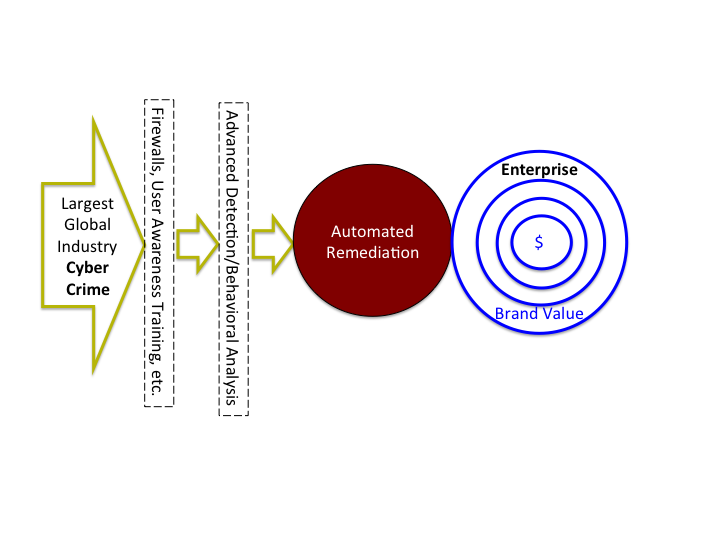
Figure 3 - Automated Remediation to combat cyber crime.
The concept of a network immune system is that large cyber systems can be thought of as similar to the human body with a skin (firewalls, etc.) keeping out most of the bad things, and an internal system that takes care of the ones that get through the skin. Stephanie Forrest proposed the concept of a network immune system 20 years ago. Now, the need for such a system has become clear and automated remediation makes it possible.
Automated remediation should be similar in concept to the human immune system. To achieve that objective in today’s cyber systems, it must have the following characteristics:
- Combination of Central/Distributed - work with system components throughout the network (central site, edge, in between, etc.);
- Connect to all - layers of technology, administrative units, vendor products – even as they change;
- Move with functions as they move - from physical to local virtual, to private cloud, public cloud, hybrid cloud, etc.;
- Deal with today’s scale – respond in second(s) to attacks on critical resources;
- Combine manual input where and when appropriate; and
- Deliver five nines performance (Telco-grade reliability).
This automated remediation capability should, much like the human immune system, be an overlay. Its objective is to be able to respond very quickly to an identified attack, in fractions of a second or several seconds at the most. To do this, it must have elements connected and physically very close to all system components. Attacks today target components at the edge, in the central site, and in between. So the automated functionality has to be able to have functionality that can perform in all of these areas. Furthermore, in today’s systems, functionality can move from: physical device, to local virtual implementation, to the cloud. Once in a cloud, it can move back and forth between private and public cloud. So, the automated remediation capability must be able to move with it.
This implies that the cyber immune system, like the human immune system, must have components distributed throughout the cyber system it is protecting. These components must be able to move around in the cyber system without being reprogrammed; interact with each other very quickly and reliably; and interact with all the interfaces/data models of the cyber system components they are protecting.
Because of its critical nature, the automated remediation capability must be functioning reliably all the time. This means that it can not be shut down for system maintenance or because of the addition or change of components in the cyber system being protected. It has to be able perform in spite of the dramatically growing data volumes and cyber system scale. Finally, no man-made system can be perfect, but the automated remediation capability should be able to meet the typical telco performance standard of five nines. That is, an up time of 99.999 percent of the time.
There is an ongoing need for manual participation in some remediation activities. But in those cases, the manual activity also needs to be supported by automated tools to be effective. As Bill Yeack, an international security expert says, “Cyber assets can be categorized by value into five levels (level one: large numbers of low value assets – to level five: small number of very high value assets). For levels one and five, you want immediate incident response with no human interaction that might cause delays. For level two through four, you may want to have a human operator review proposed responses before they are implemented.”
Innovative software technology can deliver these capabilities today. The challenge is for market participants to correctly understand what is needed and support those sources of innovation that are seeking to provide it



















