AI in Cybersecurity: The Good News and the Bad News
The State of AI-Powered Cyber Defense
An effective cyber defense includes a robust prevention strategy in combination with detection and response capabilities. AI plays a key role in both areas.
Learning-based AI cyber defense systems are most effective in attack detection, often using behavioral, pattern-matching, and contextual approaches to spot malicious activity hidden within vast amounts of legitimate activity. Some areas where learning-based AI is showing the most value are:
-
Malware Identification. Machine-learning AI can analyze the signatures of known malware and use this information to identify similar malware. They can also identify unusual or
anomalous behavior, such as a file attempting to access a resource it does not typically use.
-
Intrusion Detection. At this point, learning-based systems are essential for coping with the vast amount of activity-logging data in modern networks to find anomalous
behavior—and to reduce the chronically high number of alerts that bog down response teams with false positives.
- Phishing, BEC, and Spam Detection.AI-powered detection systems use a multidimensional approach, combining learned knowledge of content, context, behavior, sources, and so on to identify malicious emails. This is an ongoing contest as bad actors keep improving on their methods and adapt to defenses.
These applications of AI mostly pertain to attack detection—not robust prevention strategy. The challenge in attack prevention is organizations have only limited and partial visibility into the state of their defenses. They can only test their defenses in piecemeal fashion and under constraints against operational disruption. The security of a complex system can only be assured if it is thoroughly and realistically tested. Thus far, the only real-world tests of cyber defenses have come from the cyber attackers themselves—resulting in breaches where the defenses are found to be lacking. Thankfully, this is changing.
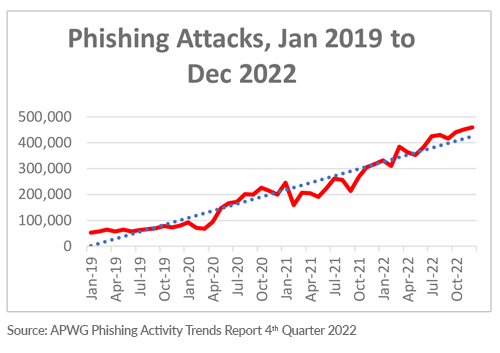
Figure 1. Phishing Activity Trends Report 4th Quarter 2022, www.apwg.org
AI in Attack Prevention
AI can play a key role in ensuring organizations are both well defended from attacks and that the potential impacts of a successful attack are minimized. This gets back to the need for robust prevention processes and tools such as those described in Gartner’s Continuous Threat Exposure Management (CTEM) program.
This is where reasoning-based AI defenses are most effective. While machine learning is based on the statistical identification of hidden patterns within a large amount of data, machine reasoning is based on using facts and relationships, and drawing conclusions from them.
This has great value in the cyber world. A semantic graph for cyber threats can be produced by using information and concepts found in standard information sources, such as MITRE ATT&CK and NVD CVE. By combining a semantic graph of cyber threats with a graph describing features of an organization’s IT systems (a “digital cyber twin” of the IT environment) the reasoning system has all the information it needs to sort through millions of simulated cyberattacks. It can identify which specific attack scenarios represent exposures to the organization and calculate the risk from those exposures. It shows the steps an organization can take to reduce exposures to an acceptable level. A CTEM process of continuous threat exposure management is made possible by AI-powered technology.
Who is Winning?
While the current state of play indicates cyber attackers are maintaining and even widening their lead, there are reasons for optimism. AI is providing organizations tools that automate many of the tasks of cybersecurity that are both costly and prone to error. AI is also enabling a more holistic approach to cyber defense, allowing businesses to better integrate security strategy and operations, thus reducing dependence on disparate point solutions. AI-powered cybersecurity is showing that organizations can improve both the effectiveness and efficiency of their security operations—lowering costs while reducing risk.