Cybersecurity Goes Mainstream
devices, and new virtualized functions can appear and move. The degrees of automation possible with technologies like SDN and NFV, along with the emergence of the Internet of Things (IoT), requires a redefinition of the term "identity". New business models enabled by these technologies further opens up service provider networks to a growing community of third-party users. Furthermore, users are accessing network resources from a variety of devices, both fixed and mobile, and from any variety of locations. Traditional, human-focused IAM systems must now accommodate people, processes, and systems.
Finding backdoors within networks can be challenging. Finding modifications to network configuration settings that create security pinholes is even more daunting. This challenge is compounded by new technologies such as SDN and NFV which bring more dynamic, programmatic network environments. Incorporating proactive network configuration discovery and auditing is more important than ever, both from a security standpoint as well as from a performance management perspective.
Check, Re-Check, Check Again and then Check Some More
VMs are typically created from templates which specify key configuration criteria including processor and memory load. In order to assure correct implementation, VMs require a “Gold Image” which defines the set of configuration parameters such as information about the Guest OS, version and patch level. It is important to proactively scan active VMs to ensure that they are properly configured when compared to the “Gold Image”. NIST explicitly recommends that the VM configuration be checked for compliance to configuration settings in these Gold Images in order to minimize configuration errors that may increase the security risk. This is distinctly different from the monitoring of inter-VM traffic. VM “Gold Image” must also be protected with strict access controls. Cloud architectures result in an elastic perimeter. More users throughout an organization, as well as trusted partners increasing risk of data leakage. Privileged user identity and account management strategies to both the hypervisor, consoles and data bases is essential.
Service providers spend considerable time and money isolating the source of network performance issues. Processes often include deploying test equipment, capturing traffic, analyzing data, only to isolate the cause of an issue to be the result of a setting on an individual router or switch. Service providers confirm that up to 60% of their network outages and degradations are caused by network configuration errors. This is only going to intensify with NFV which will bring with it orders of magnitude more configurable parameters along with more interdependencies. Ensuring that servers, the VNFs themselves, and all supporting systems are correctly configured, and stay correctly configured, is critical to assuring service delivery performance and service level agreements.
Analysis of backhaul network configuration for a mobile service provider spanning more than 10,000 different network elements or functions from multiple suppliers and close to 30 million configurable parameters identified a considerable number of configuration errors impacting subscriber experience. Numerous security vulnerabilities were also detected.
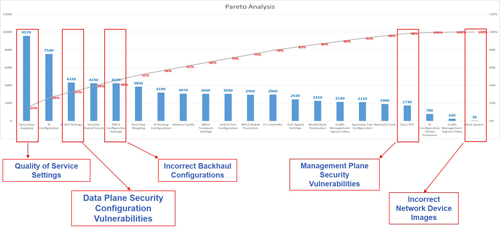
Configuration errors enable 65% of cyberattacks and cause 62% of infrastructure downtime according to a recent published research. UK headquartered service provider BT along with industry research firm Gartner estimate that 65% of cyberattacks exploit systems with vulnerabilities introduced by configuration errors. A review of Annual Incident Reports published by the European Union reveals that 25% of reported incidents in 2013 were the result of human error or malicious actions. The report goes on to cite that incidents caused by malicious actions, had long recovery times (53 hours) on average resulting in 11,600 user hours lost. Moreover, most operators do not correlate the relationship between malicious attacks and outages. The all-IP nature of modern mobile networks creates an expanded attack surface to exploit security vulnerabilities.



















