Industry Report on Telecom Fraud Management Services, Software & Strategies
By: Dan Baker
 The global village has fallen in love with the versatility that telecom industry progress has brought us. Unfortunately, there’s a trade-off because communications advances bring with them new
fraud and security risks.
The global village has fallen in love with the versatility that telecom industry progress has brought us. Unfortunately, there’s a trade-off because communications advances bring with them new
fraud and security risks.Take the business PBX. Its ability to redirect phone calls is wonderful for business people. But that feature opens the door for PBXs to be exploited through International Revenue Share Fraud (IRSF), a fraud which costs telecoms $4 billion a year according to the CFCA.
GSM is another example. It triumphed over CDMA partly because it was more versatile. Users loved the idea of popping a SIM card in and out of a handset. But that versatility also came at a cost, for it has enabled SIM box bypass, a growing fraud issue across the globe.
To explore how telecoms are keeping a lid on their old and new fraud problems, Technology Research Institute (TRI) conducted three dozen interviews with fraud management solution suppliers, service provider experts, and consultants. The result of this research is a 239-page report entitled, Telecom Fraud Management Services, Software & Strategies.
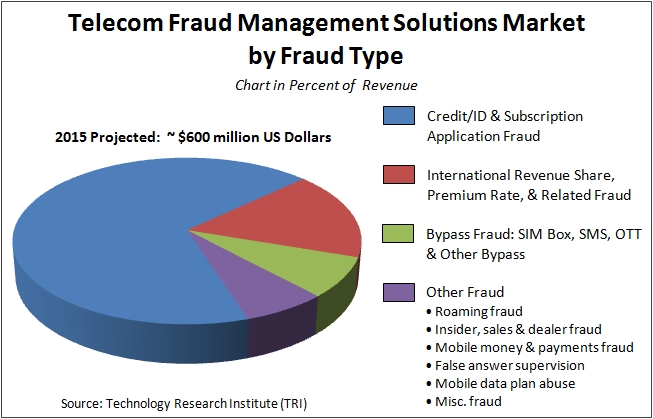
Overall we forecast the global market for telecom fraud management solutions – including software, service bureau, databases, test call generation equipment, and managed services – will reach about $600 million in 2015 as show in the forecast chart below.