Tamper-proof Computing
System-on-a chip
Freescale has been working for many years to develop their Trust Architecture now available in their QorIQ (pronounced core-IQ) and Layerscape line of system-on-a-chip (SoC) products (see Figure 1). These SoCs are available in both POWER and ARM compatible versions and are designed to run with exceptional performance and compatibility within a modern computing infrastructure.
When combined with operating systems and tools designed specifically to take advantage of the Freescale Trust Architecture, such as the Suvola LINUX Distribution, we now have the basis for tamper-proof computing, or what Freescale calls a trustworthy system. Freescale defines a trustworthy system as a system which does what its stakeholders expect it to do, resisting attackers with both remote and physical access, else it fails safe. Using the Freescale Trust Architecture, each of the six requirements for tamper-proof computing can be achieved. Let’s revisit each of those six requirements and examine how a tamper-proof platform developed on top of the Freescale Trust Architecture achieves them.
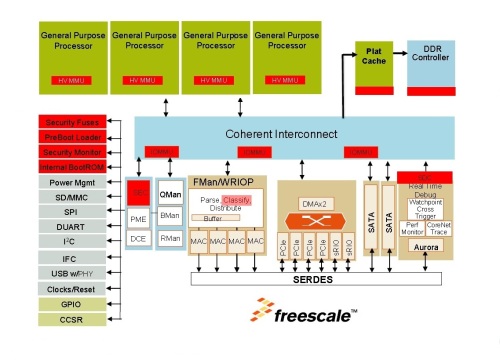
[Figure1]
Hardware cannot be added, changed or removed: During the booting up of the system, a secure boot process can detect unauthorized modifications to the system configuration, such as device trees or hardware certificates, and prevent the continuation of the boot process. Attempts to add, remove or substitute hardware prior to booting are therefore prevented. After the system is up and running, the external attachment of other devices, via USB, Ethernet or other interfaces is also detectable and these devices can be ignored or disabled to prevent the unauthorized transfer of data to or from these devices.
Software cannot be added, changed or deleted (by a single individual): To add, change or delete software requires that a user have access and permission within the computing file system. The Suvola LINUX distribution includes a file system that requires a two-party authentication system to install executable code of any type, thereby preventing the modification of executable software by a single individual. Further, all software authorized to run on a tamper-proof computing platform must be signed by the manufacturer (author), the user of the platform (stakeholder in Freescale terminology), and keyed to a secret within the SoC to guarantee its authenticity. The algorithms for software installation are known only to the Suvola software installation toolset and are rotated frequently to provide additional security.
Software cannot be injected from a remote source or via data: The computing platform provides for a run-time integrity checker, which can determine if the software about to be submitted to a CPU for execution is known to the system or not. Unknown software is simply not permitted to execute. Known software must match a series of signature and validation checks to ensure that it has not been tampered with prior to execution. While in memory, code is continuously monitored to ensure that it has not been tampered with since it was originally loaded. The SoC can also be configured (by a permanent fusing mechanism within the SoC) to disable debug interrupts, physically partition cores and memory, and close other “back doors” that can be used to alter code or execution when in production by a sophisticated attacker.



















