Protecting Cellular Infrastructure
By: Mark Cummings, Ph.D., William Yeack, CSE

Ransomware attacks can target enterprises, public utilities, government agencies, political parties, schools, hospitals, and more. Attackers are only concerned with how much money they can extort. So, all kinds of organizations need to be prepared. Preparation through ongoing preparation and management can be organized in four phases, as shown in Figure 1 and as outlined below:
- RM: Ransomware management
- R -2: Pre-attack phase: ransomware detection, intelligence, communications and defense
- R -0: Attack phase: management and response
- R +2: Loss minimization phase: asset lock up negotiation and restoration
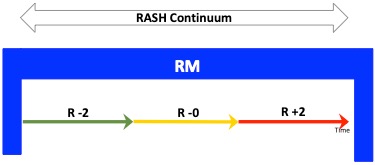
Fig. 1: The RASH Process
We explore each of the ransomware preparation process phases, developed by BCI, in more detail below.
RM - Ransomware Management
Ransomware management is a complex and event-driven process. Unfortunately, you can’t protect everything all the time. It is neither economical nor practical. First, the most critical management task is to decide what level of protection should apply for each asset. This ranking needs to be a cooperative effort across the whole organization. Many different parts of the organization will have very different ideas about what needs to be protected. Senior management must weigh in with decisions based upon sound guidelines.
Management must develop plans for “what-if” scenarios. Document the alternatives before you have to decide. Key is planning for the personnel and resource surges for an attack and documenting them, including sourcing.
Ransomware management is a continuous process that needs input from the whole organization while ensuring the confidentiality of the ransomware plans and alternatives. Management must monitor the live-fire training and testing of the entire organization. As a caution, the actual asset list and prioritization must never be used in training.
R -2 (R minus 2): Ransomware Pre-attack Phase
R -2 is the pre-attack phase. The goal of R -2 is to detect, manage, and block potential ransomware threats. The fundamental problem in this phase is the massive amount of data that needs to be analyzed. Yet lurking in the data are indicators of an attack. These indicators or “smells” in the data are very difficult to detect and require sophisticated machine learning tools. When a smell is discovered, it is fed into an attack intelligence system (AIS) that measures the probability of an attack and determines alert levels.
The attack intelligence system has many uses, including providing data to preemptively block impending threats and correct known vulnerabilities; identifying areas to thwart future attacks; detecting successful attacks; and monitoring the tempo of attack for defense resource planning
The AIS also provides the foundation to communicate the organization’s alert levels. Communications is the lifeblood of attack management and must include a broad array



















