Patent Pipeline: Securing IoT
Aggregating Decrypted Data into Data Sets
U.S. Patent No. 9,479,485 for a “Network Security Method and Network Security Servo System” was issued just last year to Wistron Corporation, a Taiwan-based provider of support services for design, manufacture and after-sales services for information and communication technology products. This patent uses encrypted and decrypted data among IoT devices to authenticate them within a network, and is a software solution.
The invention covered by this patent decrypts a plurality of encrypted data points from an IoT device, then aggregates these data points into a plurality of aggregated data sets so the aggregated data points form a plurality of data sets. It retrieves centroid data points corresponding to the data sets so that the first centroid data points form a first core data set. It then retrieves a second set of centroid data points that correspond to the first core data set and a second core data set in which the second core data set corresponds to other Iot devices. The system determines if the IoT device is an anomaly state based on the second centroid data points. It can then isolate a specific IoT device to a specific virtual network when it determines that an IoT device is in an anomaly state in much the same way that anti-virus software isolates questionable files on a hard drive. Once a suspected device is verified to be authentic, it can be released from isolation and returned to the network.
Testing Transaction Protocol to Verify a Device
U.S. Patent No. 9,510,195 for “Secured Transactions in Internet-of-Things Embedded Systems Networks” was also granted last year to the Dutch semiconductor giant, STMicroelectronics International N.V. In a world of man-to-machine and machine-to-machine interfaces, it is important to note that the technology covered by this patent is totally machine-to-machine and does not require a human interface! It is a hardware solution that uses an integrated circuit that is separate from the network to verify communications within the network by testing the integrity of the transaction’s protocol.
The patent creates a secure network-enabled device and a second security module that is an integrated circuit. The security module is initiated, and data is communicated from the secure network-enabled device via a transceiver. The security module is configured to test a subset of the data communicated to the secure network-enabled device, and the security module is configured to test the integrity of the transaction protocol that governs the stream of data bits of the data communicated to the secure network-enabled device. If the protocol does not match the established standards for the network, that device is not permitted to communicate with other devices in the Iot network. At that point, human intervention is needed to over-ride the system when it produces a false negative.
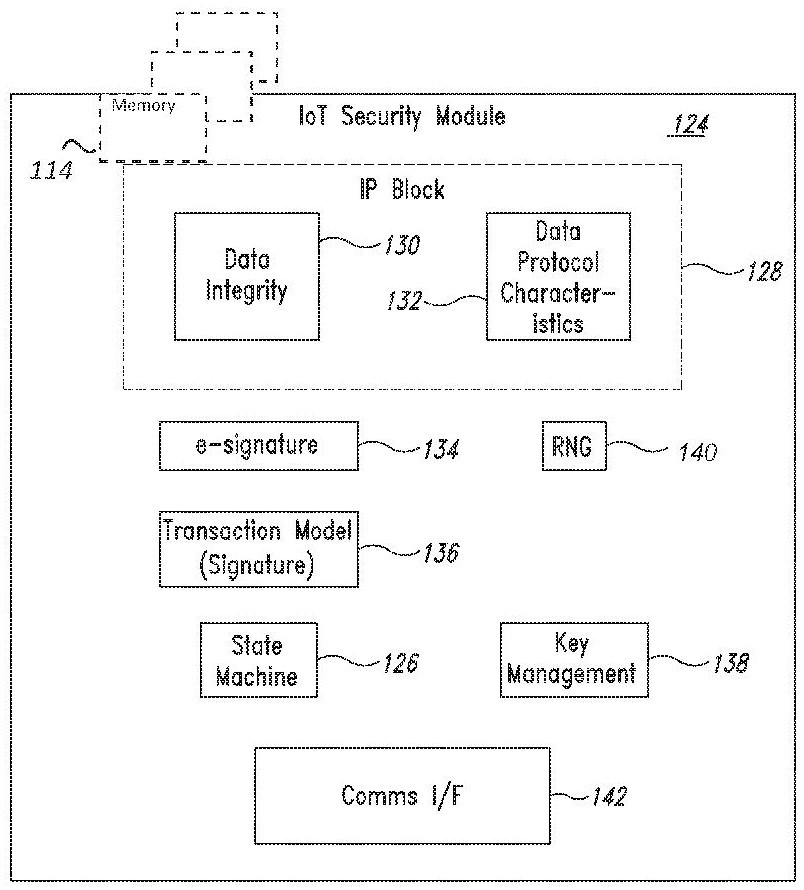
Figure 4 from U.S. Patent No. 9,510,195 is a block diagram of an IoT security module.



















