The Impact of Virtualization on Global SLAs
- Regulatory compliance: Is the cloud vendor willing to undergo external audits and security certifications?
- Privileged access: Who has special access to data? Who decides about the hiring and management of such administrators?
- Data location: Does the cloud vendor allow for any control over the location of data?
- Data segregation: Is encryption available at all stages, and were these encryption schemes designed and tested by experienced professionals?
- Recovery: What happens to data in the case of a disaster, and does the vendor offer complete restoration; and, if so, how long does that process take?
- Investigative Support: Does the vendor have the ability to investigate any inappropriate or illegal activity?
- Long-term viability: What happens to data if the cloud vendor goes out of business and its clients’ data returned and in what format?
- Data availability: Can the cloud vendor move all their clients’ data onto a different environment should the existing environment become compromised or unavailable?
Security considerations
As shown in Figure 2 below, each type of cloud – public, private, hybrid – has its own security considerations that affect authentication, authorization, data confidentiality and integrity, non-repudiation, and availability.
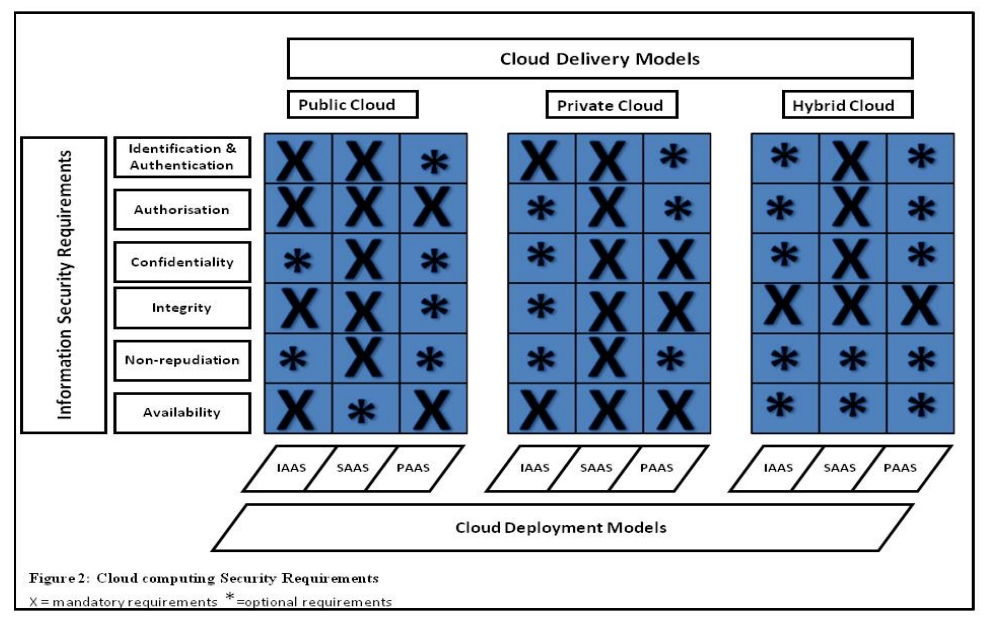
Figure 2: Cloud computing Security Requirements. Source: Platform Computing
In minimizing potential security trust issues as well as adhering to governance issues facing Cloud computing, a prerequisite control measure is to ensure that a concrete Cloud computing Service Level Agreement (SLA) is put in place and maintained when dealing with outsourced cloud service providers and specialized cloud vendors. Due to the nature and demand of emerging cloud technologies, there is a certain degree of inexperience when dealing with cloud security. Currently Cloud computing clients have to trust 3rd party cloud providers on many fronts, especially on the availability of cloud service as well as data security. Therefore, the SLA forms an integral part of a client’s first line of defense. The SLA thus becomes the solitary legal agreement between the service provider and client.



















