SD-WAN Security Options in a Multi-Cloud Architecture
By: Dave Ginsburg

As WANs become more complex and the enterprise perimeter dissolves, establishing an effective security posture becomes more complex. Be it the branch, the data center, remote workers or the cloud, each new on-ramp increases the attack surface. And, with the increasing use of software as a service (SaaS) applications, expected to reach $200 billion by 2024, backhauling all traffic to a single point is just not feasible.
Unfortunately, enterprise planners are not quite ready to migrate many of their mission-critical applications to the cloud, primarily due to gaps in integration, configuration and a general understanding of a given SaaS vendor’s security capabilities. An effective multi-cloud security architecture in the context of a managed software-defined wide area network (SD-WAN) service must therefore include this evolved connectivity and the various business processes, yet at the same time be consumable. A single breach, whether resulting from ignorance or malicious intent, is enough to bring down an organization.
Understand Connectivity Requirements
With enterprises undergoing WAN transformation and adopting SD-WAN, the best architecture is one that is manageable, well understood and universally adopted within the enterprise. The adage is that the enterprise always needs to be at the top of its game, while the hacker only needs to succeed once. In the context of WAN transformation, the enterprise needs to take stock of its connectivity requirements—what traffic stays within the branch, what is destined for HQ, and what terminates in the cloud, either within the organization’s virtual firewall, or at a SaaS application.
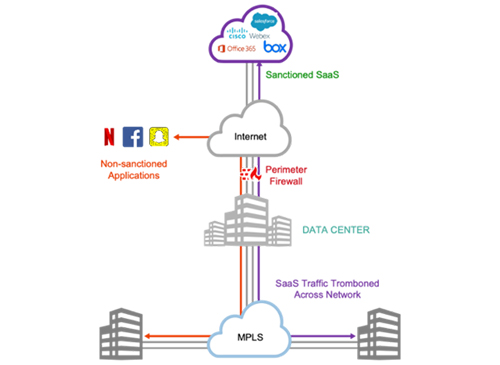
Figure 1: Legacy Architecture: Internet and SaaS application traffic backhauled (‘tromboned’)
through HQ or data center to a perimeter firewall.
Branch sites are a major consideration because legacy architectures (Figure 1, above)—where all traffic flows through a small number of larger HQ sites before heading to the Internet—don’t offer the demanded cloud agility. With SD-WAN and an Internet-first connectivity paradigm, this is even more the case. For the branch, the question becomes about what firewalling must be local (to the branch), and what can be handled within the cloud. If we consider remote workers to be no different from extended branches, the same considerations apply, with some traffic destined to the corporate intranet, while other data is carried via tunnels to SaaS applications. To repurpose the old networking phrase ‘switch when you can, route when you must,’ a modern-day equivalent could be ‘firewall in the cloud when you can, firewall at the branch when you must.’



















